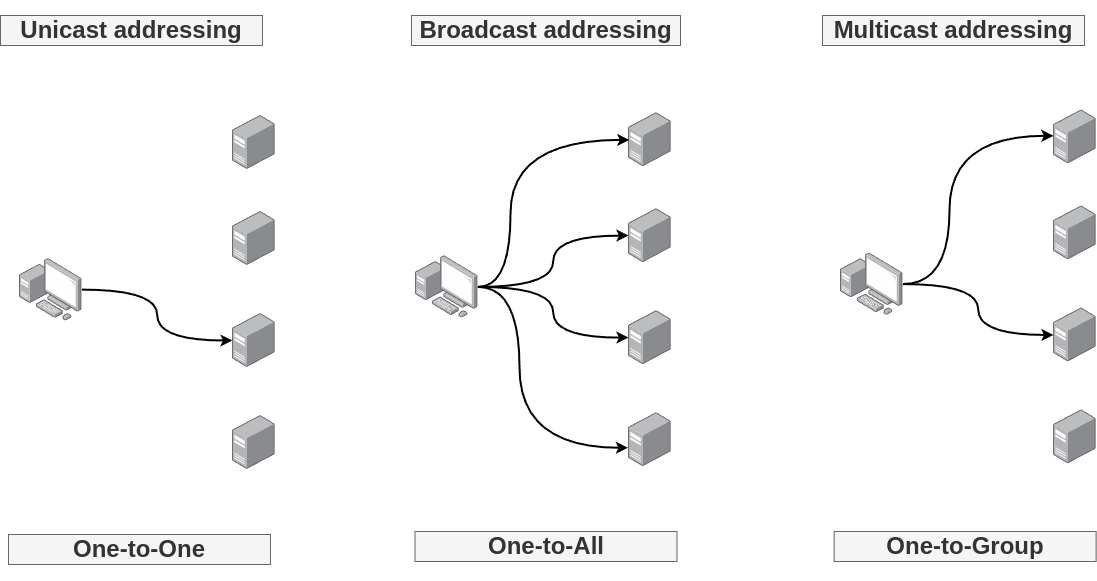
Multicasting, in the context of IP addressing, refers to the distribution of information to a group of destination computers simultaneously in a single transmission from the source. It's a more efficient method than unicast (one-to-one) or broadcast (one-to-all) communication for scenarios where the same data needs to be sent to multiple recipients. This allows for efficient and scalable distribution of data to multiple interested recipients with minimal network resource utilization.
Multicasting works by sharing an IP address between multiple devices. Any network traffic directed at that IP address will reach all devices that share the IP address, instead of just one device.
IP Multicast Group: An IP multicast group address is used to deliver packets to a group of hosts that have expressed interest in receiving data for that group. These group addresses fall within a specific range (224.0.0.0 to 239.255.255.255 for IPv4), designated solely for multicast traffic.
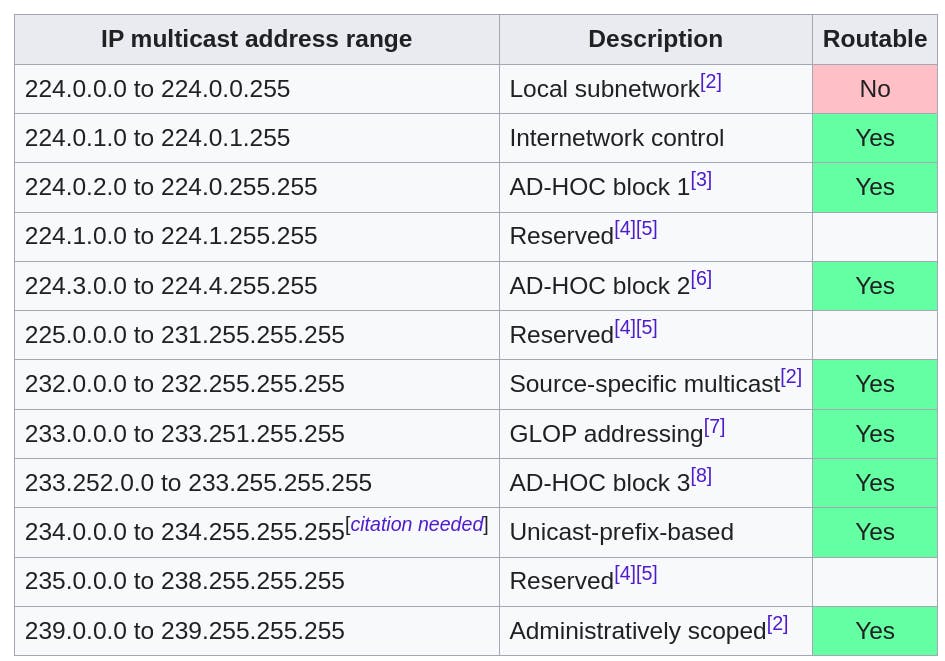
Table source: Wikipedia
Joining a Multicast Group: Hosts interested in receiving data sent to a multicast group must first "join" the group. This is typically done using protocols like IGMP (Internet Group Management Protocol) for IPv4 or MLD (Multicast Listener Discovery) for IPv6. These protocols allow hosts to inform their local router that they wish to receive traffic for a specific multicast group.
Sending Multicast Data: When data is sent to a multicast group address, the network infrastructure takes care of delivering it to all hosts that are members of that group. This involves routers and switches duplicating packets as needed to route them to all parts of the network where the interested recipients are located.
Efficiency and Scalability: Multicasting conserves bandwidth and resources since the data is sent out only once, regardless of the number of recipients. This contrasts with unicast transmission, where separate copies of the data would need to be sent to each recipient, consuming more bandwidth and processing power.
Applications: Multicast is widely used in applications that need to efficiently send data to multiple recipients, such as live video or audio streaming, online gaming, and stock market feeds. The main transport protocol for multicasting is UDP.
Control Mechanisms: Because multicast traffic could potentially flood network segments with unwanted data, mechanisms are in place (like IGMP snooping on switches) to ensure that multicast packets are only forwarded to network segments with interested receivers.
Workshop: Identify IP multicasting in your network
In this workshop, you will go through using tcpdump, a powerful command-line packet analyzer, to capture and identify multicast traffic on a network. This can be particularly useful for network administrators or anyone interested in network troubleshooting or monitoring. Before proceeding, ensure you have tcpdump installed on your system. It's available on most Linux distributions and macOS.
Step 1: Open Terminal or Command Line Interface
Open your terminal (Linux/macOS) or command prompt (Windows with WSL). You may need to run tcpdump with sudo to capture packets, as it requires root privileges.
Step 2: List All Network Interfaces
First, identify the network interfaces available on your system:
tcpdump -D
This command lists all network interfaces tcpdump can listen on. Find the interface that you're connected to the network with. It might be something like eth0 for a wired connection or wlan0 for wireless.
Step 3: Capture Multicast Traffic
To capture multicast traffic on a specific interface, use the following command, replacing <interface> with the name of your network interface:
sudo tcpdump -i <interface> ip multicast
For example:
sudo tcpdump -i eth0 ip multicast
This command captures IP packets that are multicast (destined for a multicast address).
Step 4: Analyze the Output
When you run the command, tcpdump starts displaying packets that match the filter (multicast in this case). Each line represents a packet, showing details such as the timestamp, source IP, destination IP (the multicast address), and other protocol-specific information.
Example output might look like:
12:34:56.789012 IP host1.example.com > 224.0.0.1: igmp: group 224.0.0.1
This line shows a packet sent from host1.example.com to the multicast address 224.0.0.1, which is a reserved multicast address often used for IGMP queries.
Step 5: Stop the Capture
To stop capturing packets, simply press Ctrl + C in the terminal. tcpdump will summarize the number of packets captured and analyzed.
Step 6: Narrowing Down
If you're interested in a specific type of multicast traffic (for example, SSDP which typically uses 239.255.255.250), you can refine your tcpdump command:
sudo tcpdump -i <interface> dst 239.255.255.250
This command filters packets destined for 239.255.255.250, the SSDP multicast address.
Tips for Further Analysis
Saving Captures: You can save the packet capture to a file for later analysis with Wireshark or another packet analysis tool using the
-woption, e.g.,sudo tcpdump -i eth0 ip multicast -w multicast-capture.pcap.Verbose Output: Use the
-v,-vv, or-vvvoptions for increasingly detailed packet information.Filtering by Protocol: You can add protocol filters, such as
tcporudp, to focus on specific types of traffic, e.g.,sudo tcpdump -i eth0 ip multicast and udp.
Note
Running tcpdump may generate a significant amount of output, especially on busy networks. It's often helpful to redirect the output to a file or use specific filters to limit the capture to only the most relevant data.


