Amazon S3 Access Points are a feature within Amazon S3 (Simple Storage Service) that simplify the management of data access at scale for applications or for any AWS service using shared data sets on S3. Each access point is a unique network endpoint (hostname) with its own access policies that describe how data can be accessed through the access point.
Customers with shared datasets including data lakes, media archives, and user-generated content can easily scale access for hundreds of applications by creating individualized access points with names and permissions customized for each application. Any access point can be restricted to a Virtual Private Cloud (VPC) to firewall S3 data access within customers’ private networks, and AWS Service Control Policies can be used to ensure all access points are VPC restricted. S3 Access Points are available in all regions at no additional cost.
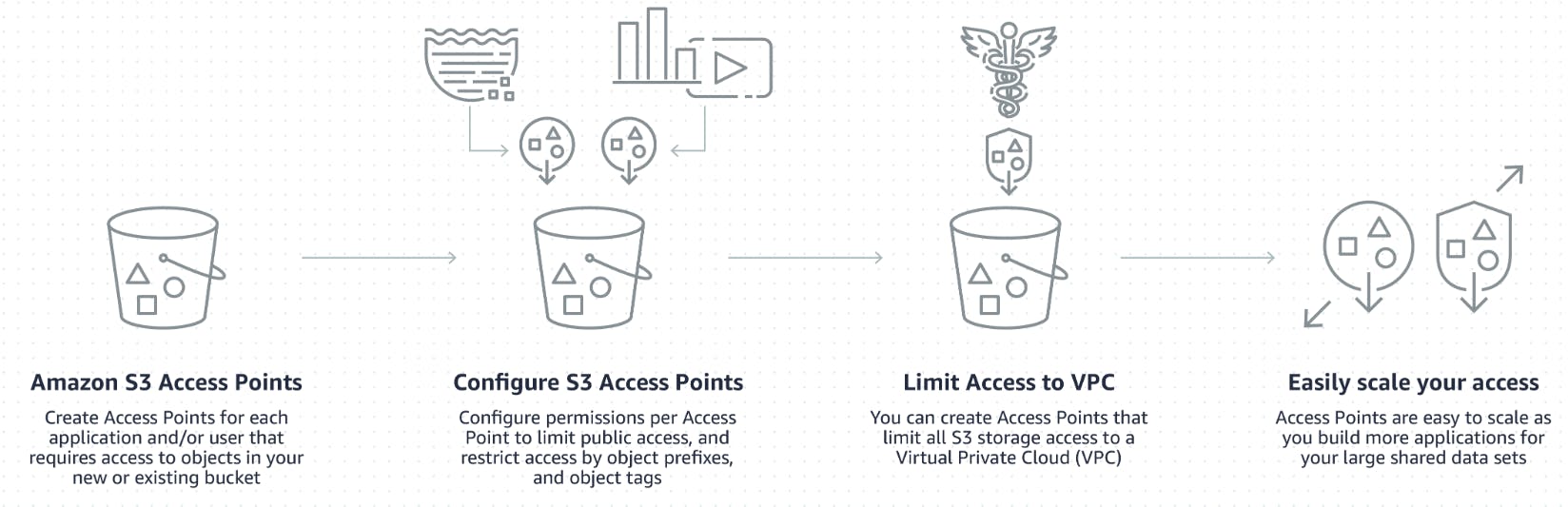
How do S3 Access Points work?
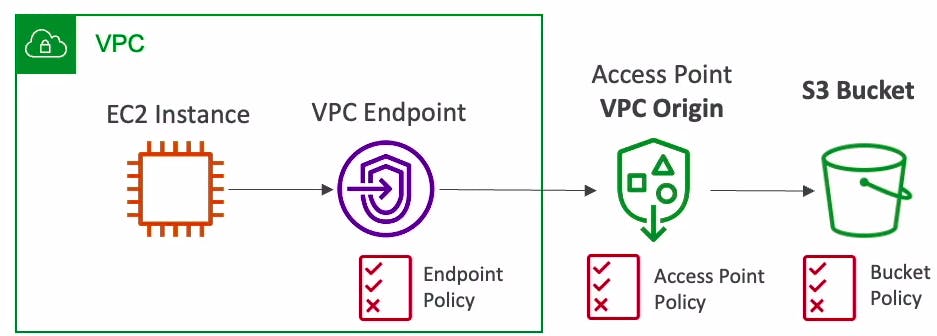
Every access point is associated with a single bucket and contains a network origin control, and a Block Public Access control. For example, you can create an access point with a network origin control that only permits storage access from your Virtual Private Cloud, a logically isolated section of the AWS Cloud.
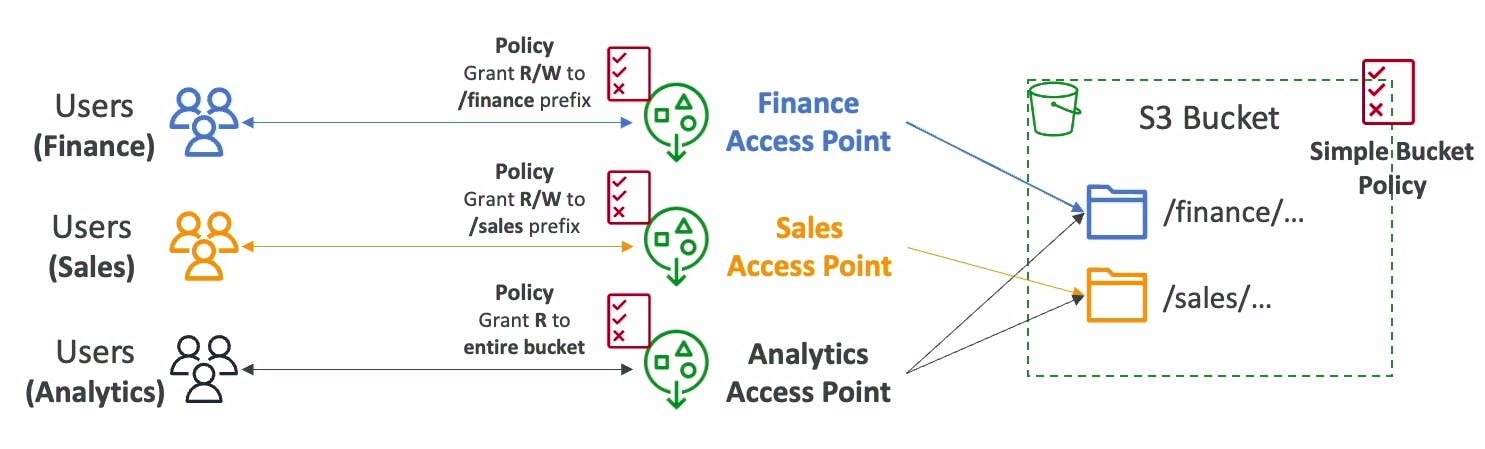
You can also create an access point with the access point policy configured to only allow access to objects with a defined prefixes or to objects with specific tags. For example, you can restrict access to the specific S3 prefixes in your bucket by using different access point policies for each endpoint. Each prefix can represent a specific department in your organization:
If you wish to provide public access to your data using access points, you must turn off Block Public Access at the bucket level. All new buckets have Block Public Access turned on by default.
You can access data in shared buckets through an access point in one of two ways. For S3 object operations, you can use the access point ARN in place of a bucket name. For requests requiring a bucket name in the standard S3 bucket name format, you can use an access point alias instead. Aliases for S3 Access Points are automatically generated and are interchangeable with S3 bucket names anywhere you use a bucket name for data access. Every time you create an access point for a bucket, S3 automatically generates a new Access Point Alias. For the full set of compatible operations and AWS services, visit the S3 Documentation.
Benefits of using S3 Access Points
Simplified Access Management
Custom Access Policies: You can define specific access policies for each access point, tailoring them to the needs of different applications or user groups. This granular control allows for more precise permission management compared to managing permissions solely at the bucket level.
Dedicated Endpoints: Each access point provides a unique endpoint for accessing S3 data, which can help in segregating and managing traffic for different applications or use cases more effectively.
Enhanced Security
Fine-Grained Permissions: By creating specific access points for different access patterns or user groups, you can apply the principle of least privilege more easily, granting only the necessary permissions to each entity.
VPC Support: Access points can be configured to be accessible only within a Virtual Private Cloud (VPC), enhancing the security of your S3 data by ensuring that it can only be accessed from a private network.
Scalability and Performance
Scale with Applications: As your application or user base grows, you can create additional access points to manage access more efficiently, without the need to reconfigure your underlying S3 buckets.
Optimized for High Volume Operations: Access points are designed to handle a large number of requests, making them suitable for applications with high throughput requirements.
Use Cases
Multi-Tenant Applications: For applications serving multiple tenants, such as SaaS platforms, you can create an access point for each tenant to manage their data access securely and independently.
Data Lakes: In data lake architectures, access points can help manage access to shared datasets across different analytics and machine learning applications.
Secure File Sharing: For scenarios requiring secure file sharing within or across organizations, access points can provide a controlled and secure way to manage access.
Copy data securely: Copy data securely at high speeds between same-region Access Points using the S3 Copy API using AWS internal networks and VPCs.
Restrict access to VPC: An S3 Access Point can limit all S3 storage access to happen from a Virtual Private Cloud (VPC). You can also create a Service Control Policy (SCP) and require that all access points be restricted to a Virtual Private Cloud (VPC), firewalling your data to within your private networks.
Test new access policies: Using access points you can easily test new access control policies before migrating applications to the access point, or copying the policy to an existing access point.
Limit access to specific account IDs: With S3 Access Points you can specify VPC Endpoint policies that permit access only to access points (and thus buckets) owned by specific account IDs. This simplifies the creation of access policies that permit access to buckets within the same account, while rejecting any other S3 access via the VPC Endpoint.
Provide a unique name: S3 Access points allow you to specify any name that is unique within the account and region. For example, you can now have a “test” access point in every account and region.
Workshop: Create Amazon S3 access point and test the connection
This exercise will guide you through the process of creating an S3 bucket, setting up access points, and testing access using those points.
Step 1: Setup and prerequisites
AWS CLI: Make sure you have the AWS Command Line Interface (CLI) installed and configured on your machine. Installation instructions can be found at https://aws.amazon.com/cli/
IAM User: Ensure you have an IAM user with permissions to create and manage S3 buckets and access points. Attach policies like
AmazonS3FullAccesstemporarily for this exercise.
Step 2: Create an S3 Bucket
Create Bucket: Run the following command to create a new S3 bucket. Replace
your-bucket-namewith a unique name for your bucket andyour-regionwith the AWS region you want to create your bucket in:aws s3 mb s3://your-bucket-name --region your-region
Verify Bucket Creation: To confirm that your bucket was successfully created, you can list all buckets in your account by running:
aws s3 lsThis command will list all S3 buckets in your account, and you should see the bucket you just created in the output.

Step 3: Upload Sample Data
Upload Files: Use the
aws s3 cpcommand to upload a file to your S3 bucket. Replacepath/to/your/filewith the actual file path on your local machine andyour-bucket-namewith the name of your S3 bucket. If you're uploading to a specific folder within the bucket, append the folder name to the bucket name (e.g.,your-bucket-name/your-folder).aws s3 cp path/to/your/file s3://your-bucket-name/Verify Upload: To check that your files have been successfully uploaded, list the contents of your bucket:
aws s3 ls s3://your-bucket-name/
Step 4: Create S3 Access Points
Access Points: In the S3 console, find the "Access Points" section in the sidebar.

Create Access Point: Click on "Create access point." Give it a name, select the bucket you created, and configure its settings:

VPC Configuration (Optional): For this exercise, you can skip VPC configuration to allow public access. For real applications, restrict access to a VPC for enhanced security.

Access Point Policy: Write a simple policy that grants read-only access to the access point. You can use the policy generator or provide a custom policy. Here’s an example policy that allows
s3:GetObjectaction from the access point:
{
"Version":"2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<account-id>:user/<username>"
},
"Action": ["s3:GetObject"],
"Resource": "arn:aws:s3:<region>:<account-id>:accesspoint/<access-point-name>/object/<username>/*"
}]
}
Replace <region>, <account-id>, and <access-point-name> with your details. For more examples of access point policies, see Configuring IAM policies for using access points.
Create: After configuring your access point, click "Create."

Step 5: Delegate access control to access points
Now we need to delegate access control for a bucket to the bucket's access points. This means that all access policy checks will go through access point policies and not the bucket policy. This is a recommended way to configure your buckets for all use cases that don't require direct access to the bucket.
{
"Version": "2012-10-17",
"Statement" : [
{
"Effect": "Allow",
"Principal" : { "AWS": "*" },
"Action" : "*",
"Resource" : [ "<Bucket ARN>", "<Bucket ARN>/*"],
"Condition": {
"StringEquals" : { "s3:DataAccessPointAccount" : "<Bucket owner's account ID>" }
}
}]
}
Replace <Bucket ARN> and <Bucket owner's account ID> with your details. For more details, see Delegating access control to access points.
To add the policy to the S3 bucket:
Save this policy in a file on your computer. For this example, let's assume you've named it
bucket-policy.json.Run the following command to apply the bucket policy. Replace
your-bucket-namewith the name of your S3 bucket andpath/to/bucket-policy.jsonwith the path to the policy file you just saved:aws s3api put-bucket-policy --bucket your-bucket-name --policy file://path/to/bucket-policy.jsonCheck Bucket Policy: To ensure your policy was applied successfully, you can retrieve the current policy attached to your bucket with:
aws s3api get-bucket-policy --bucket your-bucket-name
Step 6: Test Access Point
- List Objects Using Access Point: Use the following AWS CLI command to list objects through the access point:
aws s3api list-objects --bucket arn:aws:s3:region:account-id:accesspoint/access-point-name
Replace region, account-id, and access-point-name with your actual information.
- Download an Object: Attempt to download an object using the access point with the AWS CLI:
aws s3api get-object --bucket arn:aws:s3:region:account-id:accesspoint/access-point-name --key file-name.txt file-name-downloaded.txt
Replace file-name.txt with the name of a file you uploaded and adjust the ARN details as necessary.

Step 7: Review and Cleanup
Review: Check if you were able to list and download files using the access point as expected. This confirms that the access point is working correctly.
💡If you still can access your S3 bucket directly, then review the IAM policies attached to your user or role to ensure they don't provide broad access to the S3 resources apart from bucket and access point policies.Cleanup: Remember to delete the access point and S3 bucket after the exercise to avoid incurring unnecessary charges.
This workshop exercise offers a basic introduction to using S3 Access Points. For more complex scenarios, such as creating VPC-restricted access points or implementing more sophisticated access policies, refer to the AWS documentation.


